Routers network hardware
Configure logging on routers, switches, and network devices based on Cisco IOS, PIX-OS (ASA), and other network device operating systems.
Papertrail Setup
Papertrail supports two ways of identifying a device:
- logging to a user-specified syslog port, which is supported by most device operating systems. See Add Systems to obtain the destination hostname and port. No other changes to Papertrail are required.
- logging to the standard syslog port (514). For this method:
- Visit Add Systems and select “I’d like to aggregate system/OS logs from something else…“.
- Under Less common setup methods below the search area, click My syslog daemon only sends to port 514.
- Provide Papertrail with this device’s Internet-facing public (external NAT) IP.
These two methods cover nearly all network devices. If neither are suitable, contact us.
Device Setup
Don’t see your device here? If it can send logs, Papertrail almost certainly can receive them. Here’s how.
- Aruba Networks Mobility Controller
- Barracuda Email Security Gateway
- Cable/DSL Modems, Wireless Routers
- Cisco IOS
- Cisco ASA and PIX
- Cisco NX-OS
- Cisco CatOS
- Cisco Meraki
- Cisco Small Business
- DD-WRT
- F5 BIG-IP (TMOS)
- Fortigate FortiOS
- Hitachi SAN (HDS VSP)
- Juniper Junos
- Juniper NetScreen
- MikroTik RouterOS
- OpenWrt
- Ruckus ZoneDirector
- Ubiquiti EdgeMAX
- Ubiquiti Unifi Controller
- Vyatta VyOS
- ZyXEL ZyWALL
Aruba Networks Mobility Controller
Since this device only supports logging to the default syslog port (514), explicitly register the device’s IP.
- Visit Add Systems and select “I’d like to aggregate system/OS logs from something else…“.
- Under Less common setup methods below the search area, click My syslog daemon only sends to port 514.
- Provide Papertrail with this device’s Internet-facing public (external NAT) IP.
Papertrail will provide a hostname to use with the Aruba controller’s “logging” command. For example:
configure terminal
logging logs.papertrailapp.com
exit
write memoryIf the device doesn’t accept a DNS name, replace logs.papertrailapp.com with its IP address from nslookup.
More: Aruba log verbosity
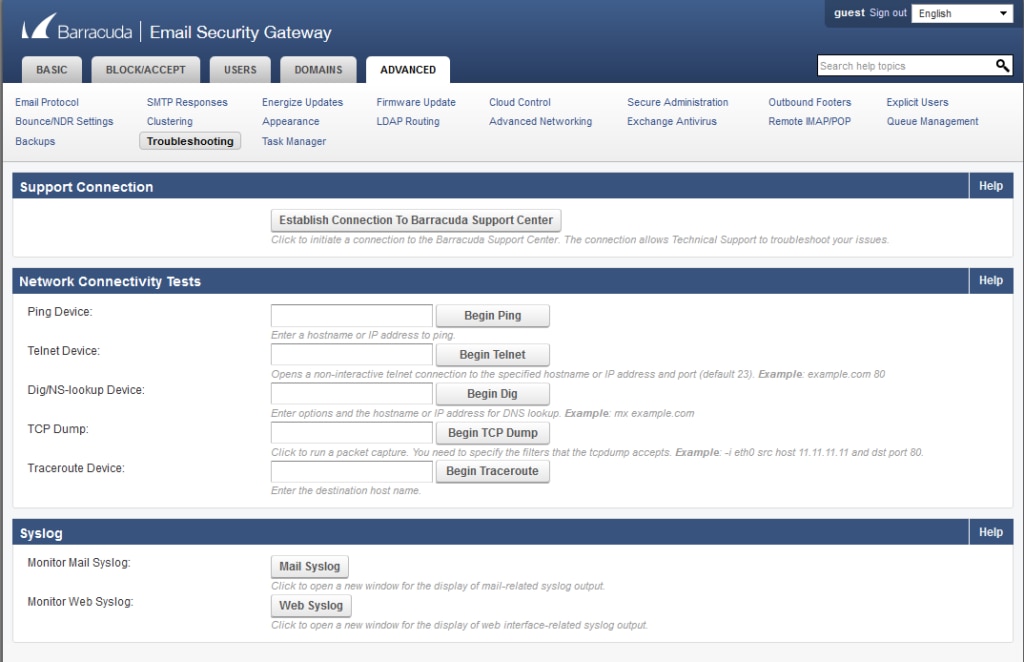
Barracuda Email Security Gateway
Barracuda Email Security Gateway (formerly Barracuda Spam Firewall) can send its Mail Syslog (SMTP activity) and Web Syslog (GUI activity) to Papertrail.
Per Syslog and the Barracuda Email Security
Gateway, browse to Advanced, then Troubleshooting. As of this writing,
Barracuda Email Security Gateway supports non-default syslog ports but only
supports logging to a destination IP address, not a DNS hostname.
To log to Papertrail, use the settings shown on Add Systems.
Instead of configuring a hostname (such as
logs.papertrailapp.com), resolve that hostname into IP addresses using
nslookup. Configure the device to log to any one of the IP addresses returned
by nslookup.
Configure the Mail Syslog or Web Syslog output:
Cable/DSL Modems, Wireless Routers
Most home wireless access points and cable/DSL routers can be configured to transmit events. In the device’s Web management interface, set the log or event destination to the hostname and port provided by Papertrail. If the device can only log to the default syslog port, 514, visit Add Systems and click the “Sender requires port 514” link.
Cisco IOS
To send from Cisco IOS-based devices, connect via SSH or telnet and run enable to become administrator. Enter the following:
configure terminal
logging host logsN.papertrailapp.com transport udp port XXXXX
logging facility syslog
logging trap debugging
exit
write memoryReplace logsN and XXXXX with the details provided by Papertrail in log destinations. Most IOS releases after 12.2 support user-supplied ports. The configuration assumes that the router has been told about DNS servers.
For older IOS versions which only support logging to the default port, the configuration could be:
logging logs.papertrailapp.comIf the device does not have DNS enabled, check the Papertrail account’s log destinations to see which hostname has been assigned, then replace logsN.papertrailapp.com with its IP address from nslookup.
We recommend the following to make IOS messages interoperate better with the syslog protocol. Disable an extra timestamp and sequence numbers:
no service sequence-numbers
no service timestamps debug uptime
no service timestamps log uptimeCisco ASA and PIX
logging enable
logging host outside logsN.papertrailapp.com udp/XXXXX
logging trap informational
logging severity 5outside is the name of the Internet-facing interface on the device. Replace logsN and XXXXX with the details provided by Papertrail in log destinations.
Informational and debug log levels can be extremely verbose (often multiple messages per NAT fixup or connection through the device).
After verifying that logging is functioning, we strongly suggest changing to a less verbose setting like:
logging trap notificationIn devices which support rate-limited logging (such as FWSM), this will rate-limit the log volume to 10 debug-level messages per 30 second interval:
logging rate-limit 10 30 level debuggingIf you explicitly register the device with Papertrail so that it can log to the default syslog port, this will work:
logging host outside logs.papertrailapp.comCisco NX-OS
On Cisco NX-OS, up to three remote syslog servers can be configured. Enter the following:
configure terminal
logging server logsN.papertrailapp.com 6 port XXXXX use-vrf vrf-name facility syslog
exit
copy running-config startup-config Replace logsN and XXXXX with the details provided by Papertrail in log destinations.
Specifying severity, VRF, and facility is optional. vrf-name will usually be either management or default, depending on which VRF has access to the internet.
Cisco CatOS
Since this device only supports logging to the default syslog port (514), explicitly register the device’s IP.
- Visit Add Systems and select “I’d like to aggregate system/OS logs from something else…“.
- Under Less common setup methods below the search area, click My syslog daemon only sends to port 514.
- Provide Papertrail with this device’s Internet-facing public (external NAT) IP.
For Cisco Catalyst OS devices, connect via SSH or telnet and run enable to become administrator. Enter the following:
set logging server enable
set logging server logs.papertrailapp.com
set logging level all 5
set logging server severity 6Device doesn’t have DNS enabled?
Instead of configuring a hostname (such as
logs.papertrailapp.com), resolve that hostname into IP addresses using
nslookup. Configure the device to log to any one of the IP addresses returned
by nslookup.
Cisco Meraki
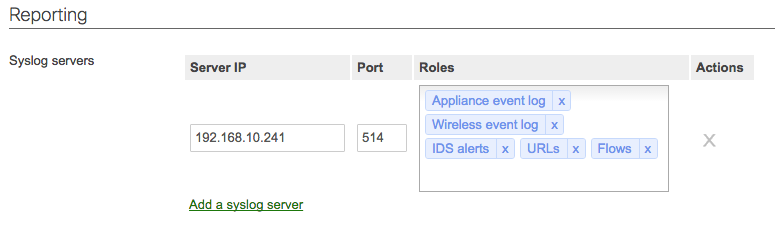
Cisco Meraki supports logging to syslog. Syslog servers can be defined in the Dashboard from Network-wide > Configure > General.
Click the Add a syslog server link to define a new server, using the port details from Add Systems. Instead of configuring a
hostname (such as logsN.papertrailapp.com), resolve that hostname into IP addresses using
nslookup. Configure the device to log to one of the IP addresses returned by nslookup.
Finally, select one or more roles that will send logs to Papertrail.
Cisco Small Business
To configure Cisco Small Business switches (e.g. SG200/SG300), log in to the web configuration utility and choose Administration > System Log > Remote Log Senders. Use the server name and port from Add Systems to define a new log server.
For more details, refer to Manage System Logs on the 200/300 Series Managed Switches or Configure Remote Log Server on a Switch, depending on the firmware version.
DD-WRT
The DD-WRT firmware package provides two different methods for configuring syslog to send log messages to Papertrail: the User Interface and via a startup script on boot.
The User Interface
Since this device only supports logging to the default syslog port (514), explicitly register the device’s IP.
- Visit Add Systems and select “I’d like to aggregate system/OS logs from something else…“.
- Under Less common setup methods below the search area, click My syslog daemon only sends to port 514.
- Provide Papertrail with this device’s Internet-facing public (external NAT) IP.
In the DD-WRT Web interface:
- Choose the “Services” tab. Enable the “Syslog” service.
- Enter the hostname provided above, such as
logs.papertrailapp.com.
Device requires an IP address, not a hostname?
Instead of configuring a hostname (such as
logs.papertrailapp.com), resolve that hostname into IP addresses using
nslookup. Configure the device to log to any one of the IP addresses returned
by nslookup.
Configure Syslog on Boot
To configure syslog to use a port other than 514, create a startup script via the router’s telnet/SSH connection and enter the following set of commands:
$ killall syslogd
$ /sbin/syslogd -l <SEVERITY> -L -R <LOG DESTINATION IP ADDRESS>:XXXXX
Check the Papertrail account’s log
destinations to see which hostname has been assigned, then replace XXXXX with the port, and
<LOG DESTINATION IP ADDRESS> with the hostname’s IP address from nslookup.
DD-WRT firmware versions other than “micro” can also send security events. To enable security events, visit the “Security” tab, scroll to “Log Management,” and enable desired options.
F5 BIG-IP (TMOS)
F5 BIG-IP runs the syslog-ng daemon as its native local log collector. Its syslog-ng can be configured to send to Papertrail. To add Papertrail as the only destination for TMOS logs (using UDP), run:
tmsh modify sys syslog remote-servers add {papertrail {host 1.2.3.4 remote-port XXXXX}}Replace 1.2.3.4 with an IP address of the log destination hostname provided by Papertrail. It can be found with nslookup. Replace XXXXX with the log destination port provided by Papertrail.
More: syslog in TMOS 9.x/10.x, syslog in TMOS 11.x, TMOS concepts
Fortigate FortiOS
Excerpting from this technical document:
To configure FortiOS to log to a syslog server via the management Web interface:
- Go to
Log&Report>Log Config>Log Setting - Select the check box beside
Syslog - Select the expand arrow beside the check box to reveal the available options.
- In
IP/FDQN, enter the log destination hostname provided by Papertrail - In
Port, enter the log destination port provided by Papertrail. - For
Minimum log level, select a log level the Fortinet unit will log all messages at or above that logging severity level. Popular values arewarning(4),error(3), ornotification(5).
Alternatively, to configure syslog via the FortiOS command line, run:
config log syslogd setting
set status enable
set server logsN.papertrailapp.com
set port XXXXX
endReplace logsN and XXXXX with the name and port number provided by Papertrail.
More: FortiOS Logging & Reporting, log message reference
Hitachi SAN (HDS VSP)
Instead of configuring a hostname (such as
logs.papertrailapp.com), resolve that hostname into IP addresses using
nslookup. Configure the device to log to any one of the IP addresses returned
by nslookup.
Set syslog server in Storage Navigator
Summarizing VSP Audit Log User Guide section 2-5 (“Transferring audit log files to syslog servers”):
- Start Storage Navigator and go to Settings > Security > Syslog
- For “Output to Primary Server,” click “Enable”
- For “Primary Server Setting,” type the IP address and port provided by Papertrail
- For “Location Identification Name,” type a name for this array
- For “Output Detailed Information,” click “Enable”
- Click “Apply”
More: VSP Audit Log User Guide (section 2-5 on page 39)
Juniper Junos
To configure Papertrail in Junos, run:
configureto enter configuration mode. Enter these configuration commands, replacing logsN and XXXXX with the name and port provided by Papertrail:
set system syslog host logsN.papertrailapp.com any notice
set system syslog host logsN.papertrailapp.com authorization info
set system syslog host logsN.papertrailapp.com port XXXXX
commit and-quitConfirm the settings with:
show system syslog host logsN.papertrailapp.com | display setJuniper NetScreen
To configure Papertrail in ScreenOS, enter these configuration commands, replacing logsN and XXXXX with the name and port provided by Papertrail:
set syslog config "logsN.papertrailapp.com"
set syslog config "logsN.papertrailapp.com" facilities local7 local7
set syslog config "logsN.papertrailapp.com" port XXXXX
set syslog enable
set syslog backup enable
set log serial-number enableMikroTik RouterOS
MikroTik RouterOS supports logging to syslog. To configure syslog via the RouterOS command line, run:
system logging action add bsd-syslog=yes name=papertrail remote=IP_ADDRESS remote-port=XXXXX target=remote
Check the Papertrail account’s log
destinations to see
which host has been assigned (it should appear as logsN.papertrailapp.com), use nslookup to find its
IP address, then replace IP_ADDRESS with that value. Replace XXXXX with the port number.
Once that’s been configured, send all or nearly all topics to the newly-created target:
system logging add action=papertrail disabled=no prefix="" topics=!async
To confirm it, run /system logging export. You should see an entry like this
/system logging action add bsd-syslog=yes name=papertrail remote=IP_ADDRESS remote-port=XXXXX target=remote
/system logging add action=papertrail topics=!async
More: RouterOS logging actions, MikroTik Wiki
OpenWrt
To configure OpenWrt to send to Papertrail, connect via SSH and then run the following:
uci set system.@system[0].log_ip=IP_ADDRESS
uci set system.@system[0].log_port=XXXXX
uci commit
Check the Papertrail account’s log
destinations to see which host has been assigned (it should appear as logsN.papertrailapp.com),
use nslookup to find its IP address, then replace IP_ADDRESS with that value.
To confirm the configuration, execute: uci show system
Ruckus ZoneDirector
Since this device only supports logging to the default syslog port (514), explicitly register the device’s IP.
- Visit Add Systems and select “I’d like to aggregate system/OS logs from something else…“.
- Under Less common setup methods below the search area, click My syslog daemon only sends to port 514.
- Provide Papertrail with this device’s Internet-facing public (external NAT) IP.
Papertrail will provide a destination hostname for your router to log
to. In the ZoneDirector Web management interface, browse to Configure > System.
Scroll to “Log Settings.” Enable “Remote Syslog.”
Instead of configuring a hostname (such as
logs.papertrailapp.com), resolve that hostname into IP addresses using
nslookup. Configure the device to log to any one of the IP addresses returned
by nslookup.
Ubiquiti EdgeMAX
The EdgeMAX router supports logging to a destination hostname and port. Log in to the router and choose the System tab at the bottom of the screen. Look for the Management Settings heading and enter your account’s destination under System Log.
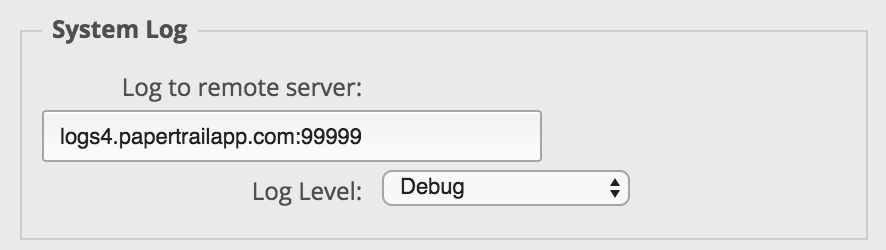
Click Save at the bottom and the setting will be applied.
Ubiquiti UniFi Controller
The UniFi Controller supports logging to a destination hostname and port. Log in to the Controller and choose the
Settings gear  . Under Remote Logging, enter
your account’s destination and port.
. Under Remote Logging, enter
your account’s destination and port.
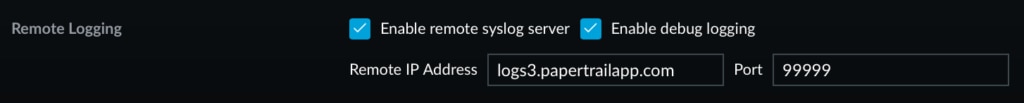
Click Apply Changes and the destination settings will be pushed to all devices under the UniFi controller’s watch including access points, switches, and routers.
Vyatta VyOS
Since this device only supports logging to the default syslog port (514), explicitly register the device’s IP.
- Visit Add Systems and select “I’d like to aggregate system/OS logs from something else…“.
- Under Less common setup methods below the search area, click My syslog daemon only sends to port 514.
- Provide Papertrail with this device’s Internet-facing public (external NAT) IP.
Papertrail will provide a destination hostname for your router to log to. Provide that hostname to the VyOS router with:
set system syslog host <hostname>
You may also want to set the log facility and/or level of log messages which are sent to Papertrail. See Brocade Vyatta 5400 manual or VyOS user guide:
ZyXEL ZyWALL
To configure ZyWALL to send to Papertrail, connect via SSH or telnet and then run:
enable
configure terminal
logging syslog 1 port XXXXX
logging syslog 1 format cef
logging syslog 1 address logsN.papertrailapp.com
exit
write
exit
Replace XXXXX and logsN with Papertrail-provided values from log destinations.
See ZyXEL Knowledge Base.
Other device
Papertrail supports the industry standard remote syslog protocol, which is the protocol used by nearly all network devices.
To send logs from a device not shown here, consult the device manual
under “Logging” or “Syslog,” or search Google
for the device name plus the word “syslog.” For example,
juniper qfx syslog or hp procurve syslog. Most device manufacturers
publish this documentation.
Follow the manufacturer’s instructions for remote logging. Use the Papertrail hostname and port shown on Add Systems.
The scripts are not supported under any SolarWinds support program or service. The scripts are provided AS IS without warranty of any kind. SolarWinds further disclaims all warranties including, without limitation, any implied warranties of merchantability or of fitness for a particular purpose. The risk arising out of the use or performance of the scripts and documentation stays with you. In no event shall SolarWinds or anyone else involved in the creation, production, or delivery of the scripts be liable for any damages whatsoever (including, without limitation, damages for loss of business profits, business interruption, loss of business information, or other pecuniary loss) arising out of the use of or inability to use the scripts or documentation.